
Web applications are replacing traditional applications in the small business and enterprise space at an ever-increasing rate, but are they secure?
With the ever-increasing demand for efficiency and accessibility, web applications have become an integral component for any business, most commonly used for employee collaboration, access to organisations resources, customer communication, data and information management and a multitude of other uses. One of the main challenges facing organisations today is ensuring the security of these web applications.
Throughout this blog, we will take you through what web application security means, some of the most commonly faced vulnerabilities on the internet today as well as some measures to counter these weaknesses.
What is web application security?
Web application security is a branch of information security dealing with the security of web applications, websites and web servers.
With news reporting that the global application security market is expecting a growth rate of 25% during the forecast period (2019-2024), application security has become a necessity for any organisation looking to protect the confidentiality, integrity and availability of their resources.
Before looking into how to ensure the security of your web application, you should first consider what motivates attackers to compromise your web application.
Web applications are considered high-value targets by attackers mainly due to the high-value rewards such as sensitive information including research and development data, credit card details, and credentials that can be reused on other systems. The complexity of the web application code also leaves a lot of room for mistakes that hackers can capitalise on.
Automation through scripts also makes some of the most common attacks quite easy for malicious threat actors.
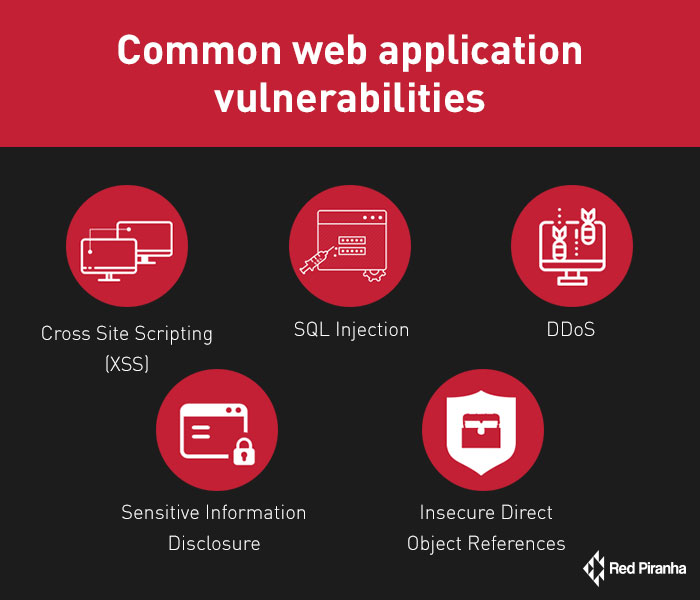
Common web application vulnerabilities
There are many web application vulnerabilities currently plaguing the internet.
A few of the most common ones that could have a significant impact on your business include:
- Cross-site Scripting (XSS) - XSS is the most prevalent vulnerability found in the wild. It enables attackers to inject client-side scripts into web pages that are viewed by unsuspecting users to steal cookies, session tokens and other sensitive information. Depending on the sensitivity of the web application’s data, this vulnerability could range from a petty nuisance to a significant security risk.
- SQL Injection - This is another widespread vulnerability found in most web applications. It occurs when user-supplied data is directly incorporated into SQL statements in the source code that interacts with the database and could lead to devastating attacks on the database including a complete dump of all data within the database, modification of records as well as full control of database server.
- Sensitive Information Disclosure - This type of vulnerability occurs when developers fail to adequately protect confidential information such as session tokens, credentials, health records or credit card numbers from parties that should not have access to that information. Attackers to leverage this information to gain unauthorised access to web applications hence critical to look out for during testing.
- Insecure direct object references (IDOR) - This is another significant vulnerability that developers are mostly unaware of but could have damaging effects if exploited by attackers. It occurs when a developer exposes a reference to an internal implementation of an object such as a database record, file, directory or key as a URL or form parameter. This could lead to loss of integrity your data as it allows attackers to modify records on the database directly.
- Distributed Denial of Service (DDoS) - This form of attack targets critical systems to disrupt a network service or connectivity to the service hence causing a denial of service to the users of that service. Experienced hackers can leverage botnets (string of connected computers all coordinated together to perform an attack) to target a single system thus making it very difficult to mitigate.
Mitigating web application vulnerabilities
Now that we’ve discussed some of these vulnerabilities, what is the best way to protect your web application against them?
Application Layer Security / Web Application Firewalls (offered by Crystal Eye)
A web application firewall helps protect web applications by filtering and monitoring traffic between a web application and the internet and can help protect against some of the previously discussed attacks. With the right web application firewall in place, attacks such as SQL injections, cross-site scripting, file inclusions among others are preventable.
According to research conducted by Gartner, an estimated 70% of all security breaches are due to vulnerabilities within the web application layer (attacks exclusively using the HTTP/HTTPS protocol). Consequently, traditional security mechanisms such as firewalls and IDS provide little or no protection against attacks on your web applications.
That’s were Crystal Eye provides detection and prevention of common attacks against web applications through our custom WAF ruleset which can prevent these to the Intrusion Protection and Detection application. This simplifies the process for protecting web applications on a network, and in instances where web applications are part of a larger network protected by Crystal Eye, these rules can be applied alongside any other ruleset to provide complete protection.
- Input / Output sanitisation - This is one of the most effective ways of preventing web application attacks. It involves filtering and validating all user-supplied data before processing. Any web application should never trust user data as it provides an entry point for exploitation.
- Enforcing cryptography - This involves ensuring that traffic between all endpoints of your application is encrypted with best encryption mechanisms, preferably TLS encryption, to prevent traffic being intercepted through man-in-the-middle attacks. It is also essential that passwords are hashed with practical hashing algorithms that provide salting to passwords as an extra layer of security.
- Web application penetration testing - Web app penetration testing is a crucial security requirement for a variety of regulatory frameworks, from PCI DSS and GLBA to HIPAA and FISMA. If you already have a live web application in production environment, conducting regular penetration tests is a necessary component for ensuring a comprehensive security assessment. It involves an active analysis of the web application for any weaknesses, technical flaws or vulnerabilities while also providing recommendations to address these issues. It is recommended to get a third-party security firm to conduct thorough penetration tests.
- Protect against DDoS - For DDoS attacks, a DDoS prevention plan based on a thorough security assessment is very crucial. This is the critical first step towards a comprehensive defence strategy. Some other key elements include; a systems checklist, a response team, defined notifications, clearly defined escalation procedures as well as incorporating a list of internal and external contacts.
In addition to applying all these mitigation measures, it is also crucial to regularly patch any external components used in your web application as vulnerabilities are reported every day to central databases such as CVE and NVD. Attackers can leverage these vulnerabilities to exploit your web application. Furthermore, it is imperative to use a security development life-cycle which involves considering and testing security at every stage of development, especially when dealing with high-sensitive data.


