
A report released by a group of cyber security researchers suggests that, Tibetan human rights NGO was targeted in what looks like a well executed phishing attack. The alleged plan was to target important people who play a major role in shaping the free Tibet cause. The sole aim of the phishing attacks was to ensure that the targets Windows PC are infected with what is known as a “customized malware”.
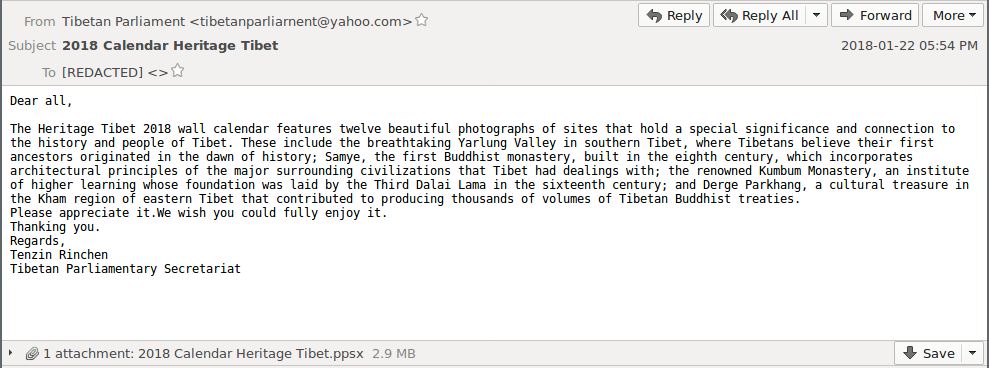
To name a few, the targets were mainly members of the Tibetan Parliament in Exile, activists, journalists and members of Central Tibetan administration. All these tier 1 personalities were supposedly attacked between January, 2018 to March, 2018. During these three months, it was noticed that the threat actors did not bother flaunting highly sophisticated hacking methodologies and tools. They rather infused simple methods and tools that might have worked for them. Given the fact that these human rights NGO are not well-funded, there are possibilities that they might have been using un-patched computers that might have got compromised.
Known Vulnerabilities Leveraged Against the Tibetan Human Rights NGO—2018 Attacks
The threat actors used phishing attacks as their primary strategy to compromise targets. The phishing e-mails were shared with the researchers who found out that the attackers made use of PowerPoint presentation and Microsoft Rich Text Format. These Microsoft office files were embedded with malware that would later turn out have the capabilities to exploit the Microsoft Office Memory Corruption Vulnerability and Microsoft Office/WordPad Remote Code Execution Vulnerability w/Windows. On further analyzing the malware, a PowerShell payload was found which was then labeled by the researchers as DMShell++. The other components of the malware is a backdoor known as TSSL and a post compromise tool named as DSNGInstaller.
Campaigns Aimed at Tibetan Parliamentary Community—2016 Attacks
Back in the year 2016, the parliamentary community of Tibet was the victim of a malware operation known as the KeyBoy. The parliamentary representatives also known as the Central Tibetan Administration were the recipients of an elaborated phishing attack deemed as a clever social engineering tactic. The attached RTF documents were embedded with malwares that exploited the buffer overflow vulnerability in the ListView and the TreeView ActiveX controls and the Memory corruption Vulnerability.
Tropic Trooper Campaign can be linked to the Attacks on Tibetan’s in 2016 & 2018
Both the campaigns leveraged against the Tibetan Nationals in the year 2016 & 2018 are connected to another campaign called the ‘Tropic Trooper’. The information gained from threat intelligence archives suggests that the Tropic Trooper malware campaign was aimed at Taiwanese and Filipino governments. It was also observed that Tropic Trooper campaign used three malwares namely, Yahamam, Yahaoyah and TSSL.
The latest campaign against Tibetan parliamentarians in 2018 can be linked to the Tropic Troopers as it adopted the TSSL malware. After elaborated research, it was found that the campaigns that targeted Tibetans in 2016 used the Keyboy malware which supposedly have its code similar to Yahaoyah.
It has also been noted that the two campaigns leveraged against the Tibetans, both targeted the Tibetan Parliamentarians. Both campaigns had a common source email tibetanparliarnent[@]yahoo.com used to send the phishing mails.
Don't let your employees fall victim to phishing attacks, get in touch with us for our Cybersecurity Awareness Training Program.
