| New Threat Detection Added | 4 (PennyWise Stealer, XWorm RAT, FormBook Malware and Ivanti Multiple Products SSRF (CVE-2024-21893)) |
| New Threat Protections | 93 |
| New Ransomware Victims Last Week | 85 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
|
Threat name:
|
PennyWise Stealer | |||||||||||||||||||||||||||
|
The PennyWise stealer has re-emerged in the cyber landscape with its updated version, v1.2, distributed through the #PureCrypter downloader. This malicious software is designed to pilfer sensitive information from infected computers, including login credentials, credit card details, social security numbers, and personal data. Once infiltrated, PennyWise may target online accounts, such as email, social media, and banking, compromising usernames and passwords. It can also harvest credit card information, birthdates, and home addresses. This malware may record keystrokes, monitor browsing history, and collect system data. Stolen information facilitates identity theft, financial fraud, and unauthorised access to personal accounts. Users should exercise caution, especially with email attachments, malicious links, and software downloads, to prevent malware infections.
|
||||||||||||||||||||||||||||
|
Threat Protected:
|
01 | |||||||||||||||||||||||||||
|
Rule Set Type:
|
|
|||||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | |||||||||||||||||||||||||||
|
Kill Chain:
|
|
|||||||||||||||||||||||||||
|
Threat name:
|
XWorm RAT | |||||||||||||||||||||||||||
|
Researchers have identified a malicious email campaign deploying the XWorm RAT, a .Net-based malware. The campaign employs embedded URLs as entry points, redirecting to a multilayer distribution with obfuscated PowerShell codes. This leads to the delivery of XWorm, utilising both "XWormV2.1" and "XWormV3.1" malware. One payload involves cryptocurrency coin hijacking, replacing legitimate addresses with fraudulent ones, and facilitating theft. The crypto ID used matches a 2021 AgentTesla campaign, suggesting the same threat actors. XWorm RAT exhibits capabilities for both crypto theft and ransomware attacks, employing a sophisticated distribution method seen in past campaigns. Robust security measures are crucial against such persistent threats.
|
||||||||||||||||||||||||||||
|
Threat Protected:
|
01 | |||||||||||||||||||||||||||
|
Rule Set Type:
|
|
|||||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | |||||||||||||||||||||||||||
|
Kill Chain:
|
|
|||||||||||||||||||||||||||
|
Threat name:
|
FormBook Malware | ||||||||||||||||||||||||||||||
|
FormBook, discovered in 2016, is an infostealer malware with a broad range of capabilities. It pilfers data from infected systems, including browser-cached credentials, screenshots, and keystrokes. Additionally, it functions as a downloader, allowing the retrieval and execution of more malicious files. Operating as Malware as a Service (MaaS), FormBook is available for purchase by cybercriminals at a relatively low cost, providing them easy access to its destructive functionalities. This malware poses a significant threat due to its versatility and accessibility, highlighting the ongoing challenges in combating cyber threats. Users should remain vigilant to safeguard their systems against potential FormBook attacks.
|
|||||||||||||||||||||||||||||||
|
Threat Protected:
|
01 | ||||||||||||||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||||||||||||||
|
Class Type:
|
Trojan-activity | ||||||||||||||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||||||||||||||
|
Threat name:
|
Ivanti Multiple Products SSRF (CVE-2024-21893) | ||||||||||||||||||
|
A server-side request forgery vulnerability in the SAML component of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) and Ivanti Neurons for ZTA allows an attacker to access certain restricted resources without authentication.
|
|||||||||||||||||||
|
Threat Protected:
|
02 | ||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||
|
Class Type:
|
Attempted-admin | ||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||
Known exploited vulnerabilities (Week 2 - February 2024)
|
Threat
|
CVSS
|
Description | |
|
CVE-2024-21762
|
9.8 (Critical)
|
Fortinet FortiOS Out-of-Bound Write Vulnerability
|
Updated Malware Signatures (Week 2 - February 2024)
|
Threat
|
Description
|
|
|
Valyria
|
A Microsoft Word-based malware which is used as a dropper for second-stage malware.
|
|
|
LokiBot
|
An information-stealer malware used to gather data from victims’ machines such as stored account credentials, banking information and other personal data.
|
|
|
DarkKomet
|
A remote access trojan that can take full control over an infected machine.
|
|
|
Qakbot
|
A malware designed to acquire valuable data such as banking credentials and is also capable of stealing FTP credentials and spreading across a network by utilising SMB.
|
| New Ransomware Victims Last Week: | 85 |
|
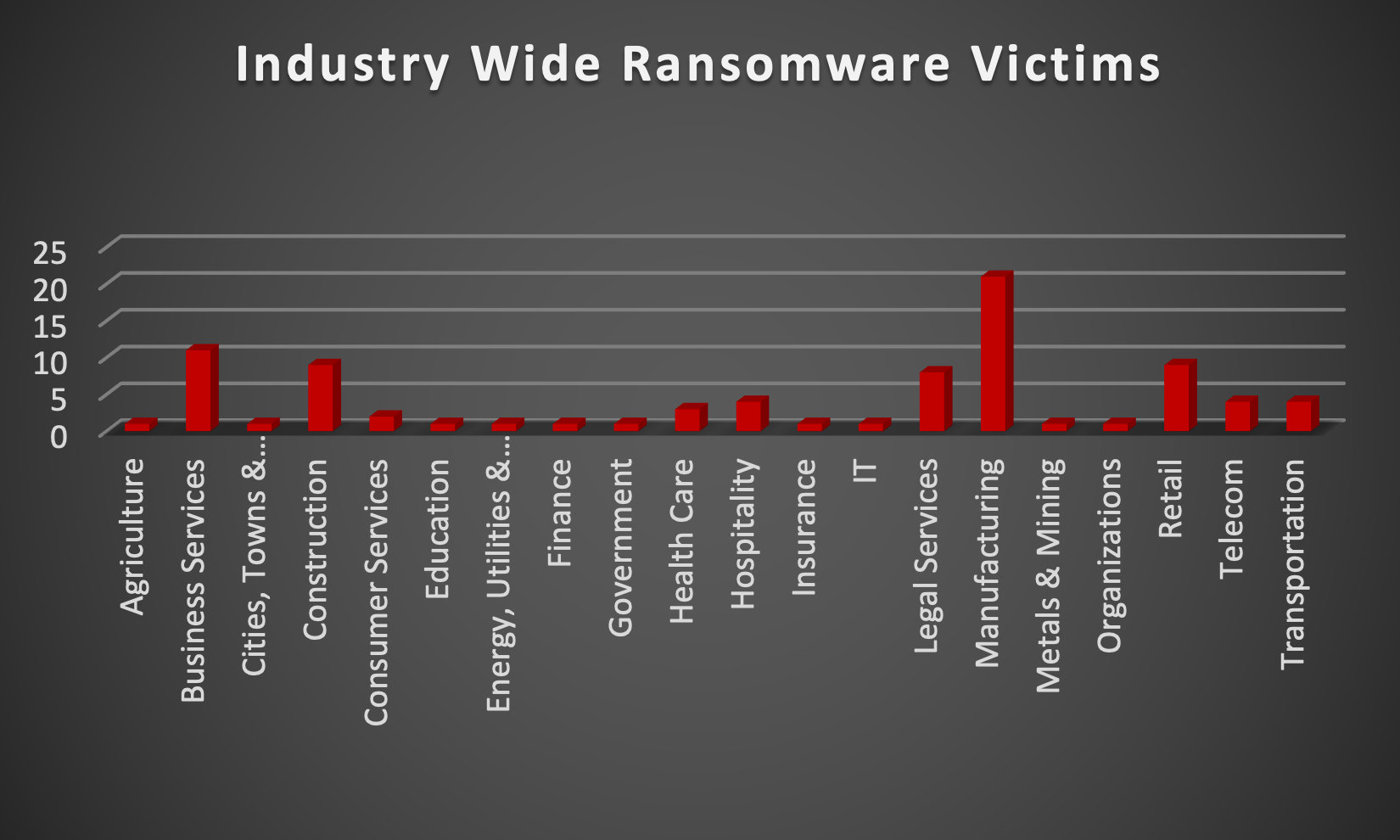
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered a total of 85 new ransomware victims or updates on previous victims across 20 different industries spanning 24 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. LockBit3.0 ransomware group stands out as the most prolific, having updated a significant number of victims (24) distributed across multiple countries. In comparison, Play and 8Base ransomware groups updated 13 and 11 victims, respectively, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. |
|
| Name of Ransomware Group | Percentage of new Victims last week |
|
3Am
|
1.18%
|
|
8Base
|
12.94%
|
|
Abyss Data
|
2.35%
|
|
Akira
|
7.06%
|
|
Alphv
|
2.35%
|
|
Bianlian
|
8.24%
|
|
Black Suit
|
3.53%
|
|
Blackbasta
|
1.18%
|
|
Cactus
|
3.53%
|
|
Clop
|
1.18%
|
|
Cuba
|
1.18
|
|
Hunters
|
1.18%
|
|
Knight
|
3.53%
|
|
Lockbit3
|
28.24%
|
|
Medusa
|
1.18%
|
|
Meow
|
1.18%
|
|
Play
|
15.29%
|
|
Qilin
|
1.18%
|
|
Ransomhouse
|
2.35%
|
|
Stormous
|
1.18%
|
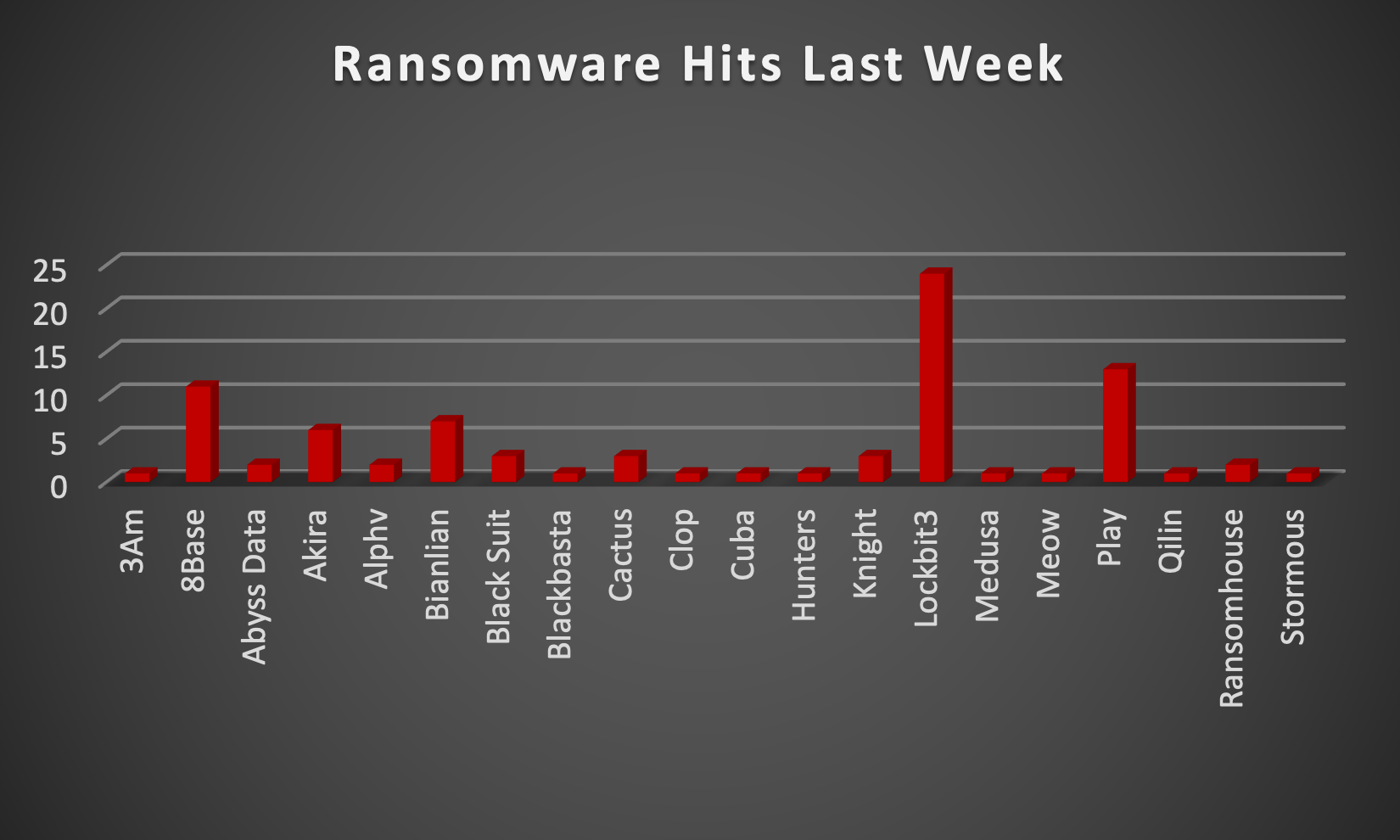
|
In a comprehensive analysis of ransomware victims across 24 countries, the United States emerges as the most heavily impacted nation, reporting a staggering 43 victim updates in the past week. The following list provides a breakdown of the number and percentage of new ransomware victims per country, underscoring the persistent and concerning prevalence of ransomware attacks, with the USA particularly susceptible to these cybersecurity threats.
|
|||||||||||||||||||||||||||||||||||||||||||||||||||
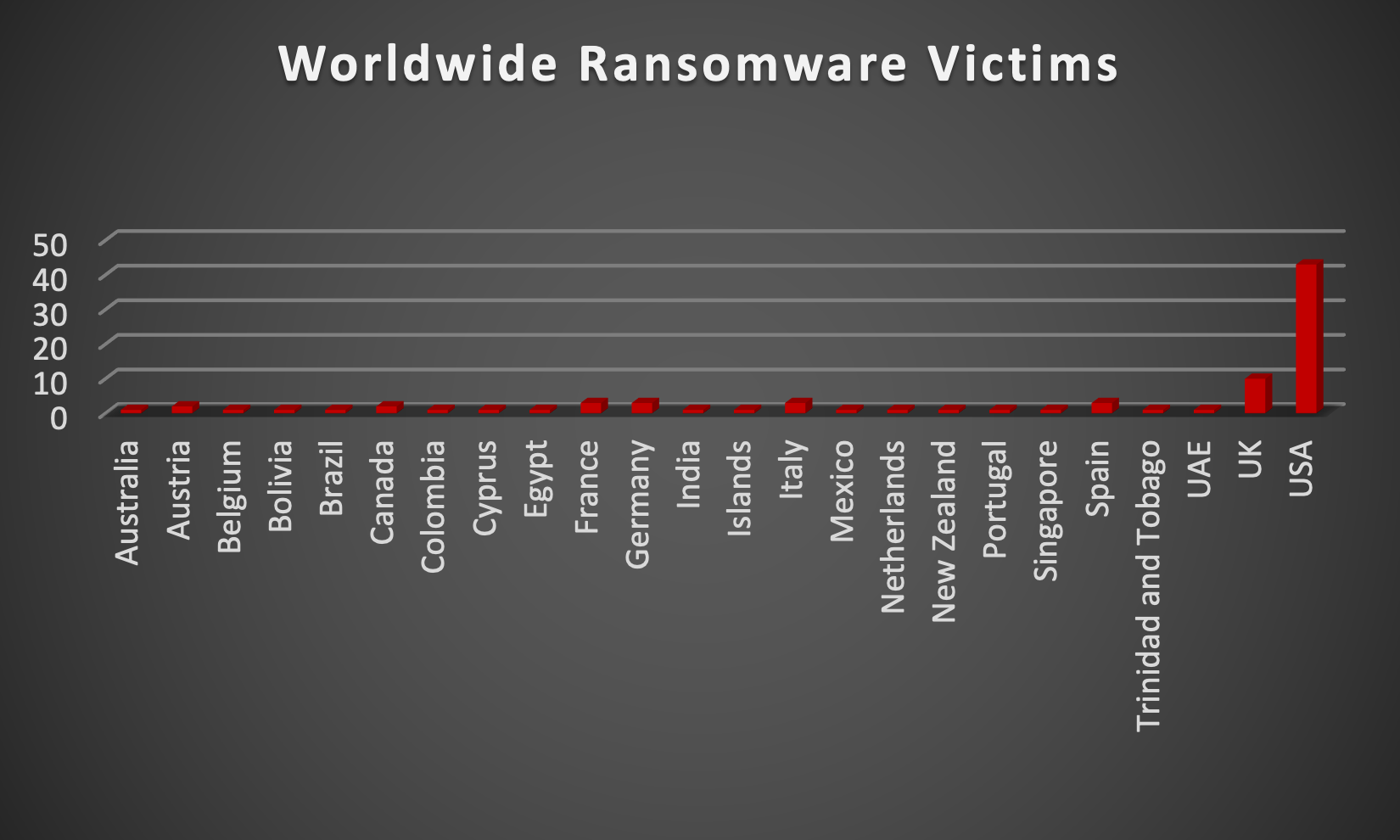
|
Upon further investigation, it has been identified that ransomware has left its mark on 20 different industries worldwide. Notably, the Manufacturing and Business Services sectors bore the brunt of the attacks in the past week, accounting for 24% and 12% of the total ransomware victims, respectively. The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
|
|||||||||||||||||||||||||||||||||||||||||||