| New Threats Detection Added | • Evilginx2 |
| New Threat Protection | 276 |
| Newly Detected Threats | 4 |
Weekly Detected Threats
The following threats were added to Crystal Eye this week:
|
Threat name:
|
Evilginx2 | ||||||||||||||||||
|
Evilginx is a go-based man-in-the-middle attack framework that’s commonly used in phishing campaigns by security professionals and threat actors. It can facilitate bypassing some MFA implementations using a reverse proxy which passes the authentication request through to the legitimate service. Evilginx uses the concept of phishlets which are customised phishing pages designed to mimic the real login page, with recent implementations utilising fake captcha style landing pages.
|
|||||||||||||||||||
|
Threat Protected:
|
16 | ||||||||||||||||||
|
Rule Set Type:
|
|
||||||||||||||||||
|
Class Type:
|
Credential-theft | ||||||||||||||||||
|
Kill Chain:
|
|
||||||||||||||||||
Known Exploited Vulnerabilities (Week 4 - January 2026)
For more information, please visit the Red Piranha Forum:
https://forum.redpiranha.net/t/known-exploited-vulnerabilities-catalog-4th-week-of-january-2026/634.
|
Vulnerability
|
CVSS
|
Description | |
|
7.8
|
Linux Kernel contains an integer overflow vulnerability that can allow an attacker with local access to escalate their privileges.
|
||
|
10
|
SmarterTools SmarterMail contains a vulnerability that can allow an unauthenticated remote attacker to upload arbitrary files to the system via the '/api/upload' endpoint. Exploitation of this vulnerability can enable an attacker to upload a WebShell providing access to the underlying system.
|
||
|
9.3
|
SmarterTools SmarterMail contains an authentication bypass vulnerability that can allow an unauthenticated remote attacker to reset the password of an administrator. This vulnerability affects version prior to build 9511. Post exploitation of this vulnerability can enable an attacker to execute operating system commands via built-in functionality, resulting in SYSTEM or root level access on the underlying system.
|
||
|
9.8
|
GNU InetUtils contains an argument injection vulnerability in telnetd that can allow a remote attacker to bypass the authentication by passing through an environment variable (USER="-f root") upon connecting. This vulnerability affects versions 1.9.3 through to 2.7, and exploitation can result in an attacker gaining root level privileges on the system.
|
||
|
7.8
|
Microsoft Office contains a vulnerability that can result in bypassing OLE mitigations when opening a arbitrarily crafted office file. This security feature protects users from executing embedded COM/OLE controls within the document.
|
||
|
9.8
|
Broadcom VMware vCenter Server contains a heap overflow vulnerability within the implementation of the DCERPC protocol that can allow an attacker with network access to execute code on the system.
|
||
|
8.8
|
Synacor Zimbra Collaboration Suite (ZCS) contains a file inclusion vulnerability within the RestFilter component that can allow an unauthenticated remote attacker to include files via a specially crafted request to the '/h/rest' endpoint.
|
||
|
9.2
|
Versa Concerto SD-WAN orchestration platform contains an authentication bypass vulnerability within the Traefik reverse proxy configuration that can allow an unauthenticated remote attacker to access administrative endpoints. This vulnerability affects version 12.1.2 through to 12.2.0, exploitation of this vulnerability can allow an attacker to access the internal actuator endpoint which provides access to heap dumps and trace logs.
|
||
|
5.3
|
Vite Vitejs contains an improper access control vulnerability within the dev server that can allow an unauthenticated remote attacker to read arbitrary file contents. Exploitation of this vulnerability may provide information that can be used in further attacks.
|
||
|
7.5
|
Prettier eslint-config-prettier contains embedded malicious code as a result of a successful phishing campaign against a maintainer of the library, which resulted in malicious packages pushed to the npm registry. The malicious code affects versions 8.10.1, 9.1.1, 10.1.6 and 10.1.7, and installation of this package results in the execution of a Windows based malware.
|
||
|
8.2
|
Multiple Cisco communication products contain a vulnerability that can allow an unauthenticated remote attacker to execute arbitrary code via a specially crafted HTTP request. Exploitation of this vulnerability can result in an attacker gaining access to the underlying system, with post-exploitation enabling elevation of privileges to root.
|
Updated Malware Signatures (Week 4 - January 2026)
|
Threat
|
Description | |
|
XWorm
|
A Remote Access Trojan (RAT) and malware loader that's commonly used in cyberattacks to give attackers full remote control over a victim's system. It's part of a growing trend of commercialised malware sold or rented on dark web forums, often under the guise of a “legitimate tool.”
|
|
|
Lumma Stealer
|
A type of malware classified as an information stealer. Its primary purpose is to steal sensitive information from infected systems, including but not limited to credentials, financial information, browser data, and potentially other personal or confidential information.
|
Ransomware Report |
|
|
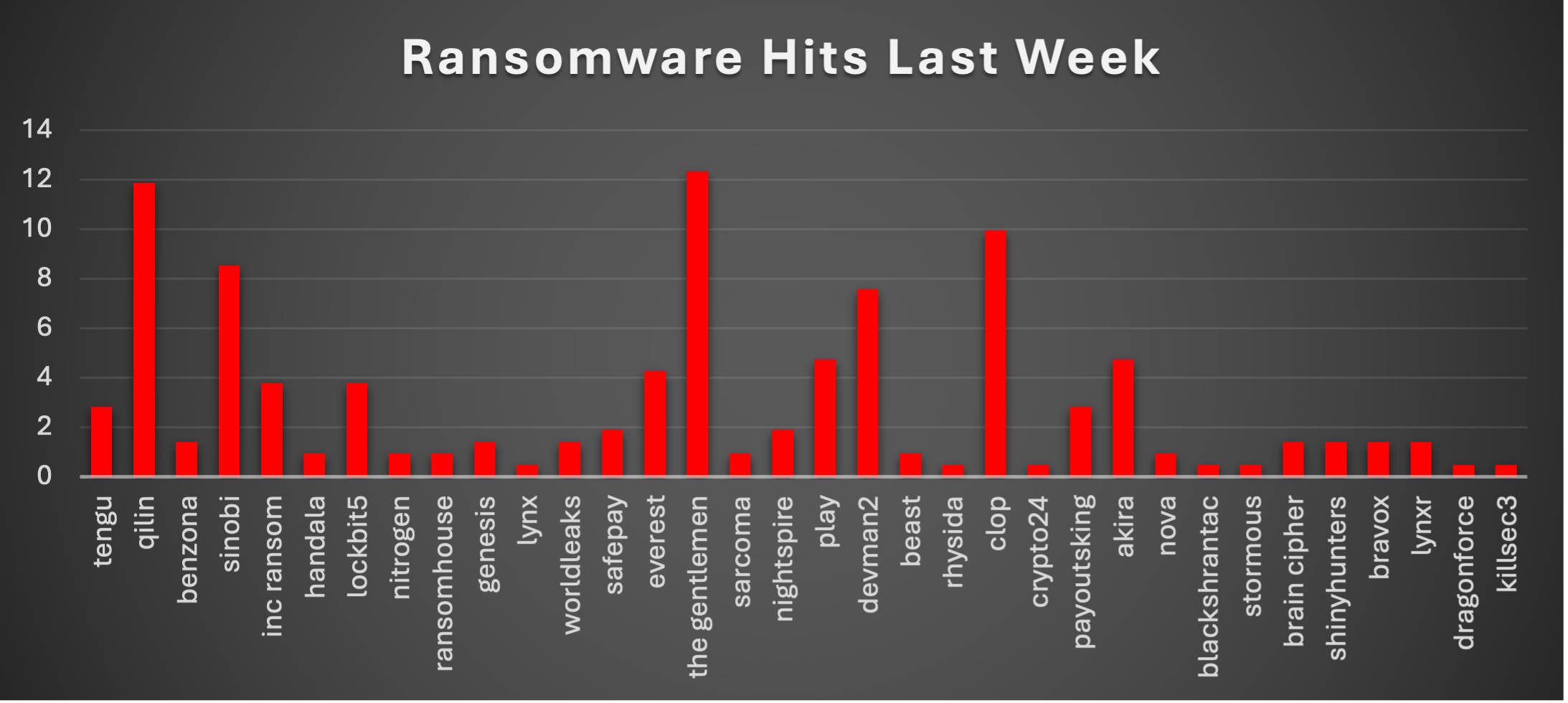
The Red Piranha Team conducts ongoing surveillance of the dark web and other channels to identify global organisations impacted by ransomware attacks. In the past week, our monitoring revealed multiple ransomware incidents across diverse threat groups, underscoring the persistent and widespread nature of these cyber risks. Presented below is a detailed breakdown of ransomware group activities during this period. Ransomware Threat Landscape (Last Week)The following chart illustrates the distribution of ransomware attacks by threat group during the analysis period. Nova accounts for 0.95% of total attacks, with 'The Gentlemen' (12.32%), Qilin (11.85%), and Clop (9.95%) leading the threat landscape. |
Nova Ransomware
Analysis Period: 17 January 2026 - 23 January 2026
Description
Nova (formerly RALord) is a Ransomware-as-a-Service (RaaS) operation first observed in late March 2025 under the name RALord, rebranding to Nova in April 2025. The group operates a double-extortion model - encrypting victim files while exfiltrating sensitive data to maximise ransom pressure. Nova maintains a Tor-based Data Leak Site (DLS) where victim profiles are published alongside countdown timers and proof-of-theft documentation. The group has claimed victims across multiple continents, targeting sectors including healthcare, education, hospitality, IT services, media and entertainment, construction, and agriculture.
Nova operates an aggressive affiliate recruitment model offering an 85/15 revenue split in favour of affiliates - one of the more generous offerings in the current RaaS landscape. Standalone locker access is available for €200–€300 (lifetime fee), lowering the barrier to entry for less sophisticated actors. The group actively recruits on darknet forums (RAMP, DarkForums) under the username "ForLord," seeking candidates with Rust/Python programming skills, CVE exploitation expertise, and network penetration experience.
Technical Profile
Ransomware Payload: Nova operates two primary payload variants:
- Affiliate variant: Appends .nova extension to encrypted files
- Premium Rust-based variant: Appends .RALord or .ralord extension
- The ransomware is written in Rust—a choice that complicates static analysis and helps evade traditional signature-based detection. Upon execution, the malware opens a console window via conhost.exe and begins scanning for files to encrypt. Ransom notes are dropped with randomised filenames directing victims to qTox for negotiation.
- Platform Support: Cross-platform capability spanning Windows, Linux, and VMware ESXi environments.
Detailed Tactics, Techniques, and Procedures (TTPs)
- Initial Access (Compromised Credentials & Vulnerability Exploitation)
Nova predominantly gains access through compromised VPN/RDP credentials obtained via credential stuffing attacks, reused passwords, or purchased from Initial Access Brokers (IABs). The group specifically targets organisations with exposed remote access services lacking multi-factor authentication.
Primary access methods include exploitation of vulnerabilities in public-facing applications (VPN appliances, firewalls, remote access gateways), spearphishing campaigns disguised as legitimate business communications (contracts, invoices), AI-powered phishing using LLMs to craft emails indistinguishable from legitimate corporate communications with localised language and tone for specific regional targets.
In a notable shift documented by FBI advisories, ransomware groups including Nova have begun recruiting corporate insiders or unwitting gig workers to physically enter offices and insert USB drives under the guise of IT help desk tasks. Nova affiliates frequently purchase valid domain administrator credentials from IABs, allowing them to bypass perimeter security entirely and begin post-compromise activities immediately.
- Execution & Operator Control
Upon achieving access, the Nova payload is typically executed via command-line interpreters including PowerShell and Windows Command Prompt (cmd.exe). The Rust-based encryptor executes via conhost.exe console window creation. Operators utilise encoded PowerShell commands to avoid detection, LOLBins (Living Off The Land Binaries) for staging and execution, and user-launched executables from downloads/temp paths. The group employs a 'fast and aggressive kill chain' philosophy, often aiming to complete the transition from initial access to full system encryption within a minimal dwell time window.
- Persistence Mechanisms
Nova establishes persistence through multiple techniques to ensure malware survives system reboots and maintains long-term presence.
Registry Modification: The ransomware creates and modifies keys within HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run to launch automatically at startup.
Scheduled Tasks: Nova creates Windows scheduled tasks that run with SYSTEM-level privileges, often set to recurring triggers like hourly intervals or user logon events.
Boot Environment Modification: A standout behaviour of the Nova cluster is the forced modification of Windows Boot Configuration Data (BCD) by executing 'bcdedit /set {default} safeboot network', forcing infected systems into Safe Mode with Networking before initiating encryption – a strategic manoeuvre designed to circumvent security software that does not load in Safe Mode.
Remote Access Tools: Deployment of legitimate tools including PuTTY, AnyDesk, LogMeIn for maintaining persistent access via stolen RDP credentials.
- Privilege Escalation
Nova operators escalate to administrative privileges before encryption. The group leadership confirmed: 'We up perms to root (admin) and run to all disks...no backups because I am encrypting with admin perm, so all backups encrypted.'
Primary escalation methods include credential-based elevation using harvested domain administrator credentials, exploitation of local privilege escalation vulnerabilities within compromised environments, and abuse of elevation control mechanisms.
They bypass User Account Control by modifying registry settings to disable Remote UAC restrictions, allowing elevated commands to be run remotely across the domain without prompting for user intervention.
- Defence Evasion (Advanced Techniques)
Nova operators are highly adept at neutralising defensive infrastructure using sophisticated evasion strategies.
Security Service Termination: The group systematically identifies and stops processes related to antivirus (AV), endpoint detection and response (EDR), and backup solutions.
Volume Shadow Copy Deletion: To prevent system restoration, Nova executes 'vssadmin.exe Delete Shadows /all /quiet' and 'wmic shadowcopy delete /nointeractive', destroying local recovery options.
Rust-Based Obfuscation: The group states 'most ransomware groups use C/C++ or Python...Windows Defender alone will capture it. Our lockers building with Rust, anti-detection.' They claim weekly locker updates to evade new Microsoft security measures. The Rust implementation generates 10,000+ functions making reverse engineering extremely difficult.
Remote UAC Bypass: Attackers modify registry to disable Remote User Account Control restrictions.
Indicator Removal: Log clearing, artifact deletion, and cleanup scripts to remove forensic evidence.
Virtualisation/Sandbox Evasion: Delays and checks for analysis tooling/VM traits to avoid sandbox detection.
- Credential Access (Aggressive Harvesting)
Nova operators aggressively pursue credential access using multiple tools and techniques.
LSASS Memory Extraction: The malware utilises tools like Mimikatz or Procdump to extract cleartext passwords and session tokens from the Local Security Authority Subsystem Service (LSASS) memory.
Browser Password Theft: Stealing credentials stored in browser password managers.
Pass-the-Hash Techniques: Using harvested NTLM hashes for authentication without needing plaintext passwords.
Token Reuse: Capturing and replaying authentication tokens for lateral movement.
Credentials from Password Stores: Extracting saved passwords from Windows Credential Manager, browser caches, and application configuration files.
- Reconnaissance & Discovery
Nova performs extensive network and system discovery to identify high-value targets.
File and Directory Discovery: Broad traversal before encryption with access spikes across network shares.
System Information Discovery: Host inventory commands, OS/domain enumeration to understand the environment.
Registry Queries: Queries related to security tooling and configurations to identify defensive measures.
Network Share Discovery: Identifying file servers, backup locations, and sensitive data repositories.
Virtualisation Storage: Specifically targeting .vhd, .vhdx, and .vmdk files within VMware and Hyper-V environments to inflict maximum operational disruption.
Cloud and Database Structures: Targeting source code repositories and database structures to increase extortion leverage.
- Lateral Movement (Enterprise Spread)
Once administrative credentials are secured, attackers pivot across the network using legitimate administrative protocols.
Remote Desktop Protocol (RDP): Primary method for interactive lateral movement across Windows systems.
SMB/Windows Admin Shares: Using ADMIN$ and C$ shares for file transfer and remote execution.
Remote Services: Leveraging WMI/WMIC for distributed commands across the enterprise.
Pass-the-Hash Authentication: Using NTLM hash-based authentication for lateral movement without plaintext passwords.
Lateral Tool Transfer: Moving tools and payloads between systems for mass deployment. SSH connections to ESXi hosts for targeting virtualisation infrastructure.
- Data Collection & Exfiltration (Double-Extortion Preparation)
Before the encryption phase is triggered, terabytes of data are exfiltrated to support double-extortion operations.
Data from Local System: Sensitive directory harvesting including PII, PHI, financial records, and business agreements.
Data Staging: Large archive staging areas with sudden disk usage spikes before exfiltration.
Archive Collection: Compressing stolen data for efficient transfer.
Exfiltration Over C2 Channel: Data theft via HTTP/HTTPS to private attacker-controlled servers.
Exfiltration Over Alternative Protocols: Using cloud services and custom transfer paths to evade detection. This data theft is central to the 'Double Extortion' model – even if a victim successfully restores from backups, the threat of leaking sensitive data provides secondary leverage to demand payment.
- Inhibit System Recovery (Backup Destruction)
As a final destructive step before encryption, Nova systematically destroys recovery options.
Volume Shadow Copy Deletion: Executing 'vssadmin.exe Delete Shadows /all /quiet' to remove Windows shadow copies.
WMI Shadow Copy Deletion: Using 'wmic shadowcopy delete /nointeractive' as an alternative deletion method.
Backup Catalogue Removal: Targeting backup software configurations and catalogues.
Backup Process Termination: Stopping backup services (Veeam, Commvault, Acronis) to release file locks. This maximises pressure on victims to pay ransom as traditional recovery methods are rendered ineffective.
- Encryption & Impact (Ransomware Deployment)
Nova employs a hybrid cryptographic scheme that balances speed with security.
Symmetric Encryption: Files are encrypted using AES-256 in Cipher Block Chaining (CBC) mode, with a unique key generated for each file to prevent batch decryption. Some variants use RC4 for faster encryption of large files.
Asymmetric Wrapping: The AES key is then encrypted with the attacker's RSA-2048 public key and appended to the end of the encrypted file, ensuring only the attacker's private key can decrypt.
File Extensions: Encrypted files receive extensions including .nova (affiliate variant), .RALord/.ralord (premium Rust variant), .LORD, .RNOVA, and variant-specific extensions like .happy11 and .KARMA.
Ransom Notes: Notes following the pattern 'README-[12 random alphanumeric characters].txt' are dropped in each encrypted directory.
- Command-and-Control / Negotiation / Data Leak
Nova maintains TOR-based infrastructure for operations and victim communications.
Data Leak Sites (DLS): Multiple active onion addresses host victim profiles with in-depth attack reports, often mockingly highlighting failed security products.
Visual Proof-of-Claims: Profiles feature screenshots of encrypted directories, internal network share listings, and samples of exfiltrated documents.
Countdown Timers: Real-time clocks indicating time remaining before full dataset release or sale to third parties.
Negotiation Portal: Secure chat environment (branded as 'Nova Access Portal') for victim communication with specialised 'journalists' and 'lawyers' who assist in drafting publication texts.
Affiliate Dashboard: Control panel tracking active infections, ransom negotiations, and exfiltration status with custom payload builders for Windows, Linux, and VMware ESXi.
MITRE ATT&CK TTP Matrix
The table below summarises Nova's tactics and techniques mapped to the MITRE ATT&CK framework:
Tactic |
Technique (ID) |
Nova Implementation |
|
Initial Access
|
Valid Accounts (T1078)
|
Stolen credentials from IABs
|
|
Initial Access
|
Phishing (T1566)
|
AI-powered spear phishing
|
|
Execution
|
Command & Scripting (T1059)
|
PowerShell/CMD, LOLBins
|
|
Persistence
|
Boot/Logon AutoStart (T1547)
|
Run keys, registry modification
|
|
Persistence
|
Scheduled Task (T1053)
|
SYSTEM-level scheduled tasks
|
|
Defence Evasion
|
Impair Defences (T1562)
|
Terminating AV/EDR processes
|
|
Defence Evasion
|
Obfuscated Files (T1027)
|
Rust 10,000+ functions obfuscation
|
|
Credential Access
|
OS Credential Dumping (T1003)
|
Mimikatz, LSASS extraction
|
|
Discovery
|
Network Share Discovery (T1135)
|
Scanning backups, VHDX/VMDK
|
|
Lateral Movement
|
Remote Services (T1021)
|
RDP, SMB admin shares
|
|
Exfiltration
|
Exfil Over C2 Channel (T1041)
|
HTTP/HTTPS to attacker servers
|
|
Impact
|
Data Encrypted (T1486)
|
AES-256/RSA-2048, .nova/.RALord
|
|
Impact
|
Inhibit Recovery (T1490)
|
vssadmin/WMI shadow deletion
|
Indicators of Compromise (IOCs)
Infrastructure / C2:
- TOR Onion Addresses:
Communication Identifiers:
- Session: 054f55ec93aca9bac362b9d91eff36a7ce451e7caba47c0b2e004ba429f9529c79
- Tox: 8E9A6195A769FE7115F087C61D75CF32874C339B3AB0947D07480C9A8A12DA5009151BE6A51F
- Telegram: @NovaSupport
Malware Samples:
- SHA-256: 456b9adaabae9f3dce2207aa71410987f0a571cd8c11f2e7b41468501a863606
- MD5: ef846baabc14fe461cff4c4a0fd5056f, be15f62d14d1cbe2aecce8396f4c6289, 4566f5ba6d1a1db0dd7794ea8d791b3f
File Indicators:
- Extensions: .nova, .RALord, .ralord, .LORD, .RNOVA, .happy11, .KARMA
- Ransom Notes: README-[random].txt, HOW_TO_RECOVER_DATA.html
- Registry: HKLM\SOFTWARE\NovaRansom
Command-Line Artefacts:
- vssadmin.exe Delete Shadows /all /quiet
- wmic shadowcopy delete /nointeractive
- bcdedit /set {default} safeboot network (EDR Bypass)
PGP:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQGNBGjOVRwBDADr6SA5p6Lqve69WGbvDlz75WD06GXKecP+koqPwj0X/a7/6D67 7zToqSE0Lm8ROBNEEZWbNdHTKiEz5MUwkWW9b4MyZeWfZ3LodE1jSHFHE6i8qQGM QzuauXpZtabJiuLeL5iBhrsNktC4Zv+T4ySQZpcT7v5VBN38tlF2UA3m1arGTE75 W7Ew+TgqYOpRnOW8Rlnc1JNh+tPszcWwzSmJRUkW5oJX79EQPu1FOot3befVQy0W TViYedsJ4TvHJZ8CAivJ/+DsMIhl6UG0wli5w2KeGNVsWPIQCTYOzCO2B7qSEGSM tb7HVp6k7Dvi2yZWRm99iUyanZ5cGpqlPyXEtaHZ7eOrQRMTKo71Zt+lrlCjePrq U/ik7Sq6o9zyFaTzCe1KOWXV06/amNgj0lC0S4hGLiCSFkfOKDR6xrBzs70x3AVD /IRXczW7vCz34myJ2QQVqt/oIqpohcHPAV+rrmfWgnEYXHt5oPhSlijmNzCrrYGl hNZWvqBRkUBuLQ0AEQEAAbQmbm92YSAoTm92YV9TdGFyKSA8bm92YTFAb25pb25t YWlsLm9yZz6JAdEEEwEKADsWIQRZdCIjGnML+3TBQwqTUHMmkHWCIAUCaM5VHAIb AwULCQgHAgIiAgYVCgkICwIEFgIDAQIeBwIXgAAKCRCTUHMmkHWCIC2FDADRZW7g CHY4HwvFrzj9FZ8UCBKpEMe2L8XXGRGvQFqos0tOExAWoon8G3QX4BzzMFxLZMpm pyAHoiRakKw8yMxONLnc2CxeKjUduEgOflW+a3InlO9EiktQXvzpW4wVafRFqPH2 JYroOplV+eghJ5f/I6VjokztS1f/OIczDdram6KbzsrOUfaHrRLMWlSpgNQcPeth XMcnuy5cs1ja85KL7OpaRnvqQTaeG2bZu/NN4F4KO7WJz7mtyUB0cbFB1S5ADac9 yK5ZRETLt34Zt2v3WPjYKQa6cAq1lUDLMhvVUKCzIT6n+hOJKdnYPJH3vJP/L6vF QVzoifoY+Xsd3h+6JD8G/LrlxV1kCnNcekG0bEDV83/aY0eiDd7KfqKfF9QciosH Q+0tdDKqQlHmAem5V9h0otqfH1ENUpk6tj4Tlnn/8MovZvQxWLgSbPGF9VG/smmY /BIH5t6ODn8/QQ8F9bqptARWe33rny+5mjeVhNV3+3pw/ldk8eKMaX6j5V+5AY0E aM5VHAEMALI7HRwcKn22nZZKBMHkOUKU5AbABSNQI0CsceLbRu3slat3Bab3rHEu 9yKM08e7/j3NzTffA61MhScTmIgi6fxgojVNKvHVC9m9YyGUOwW49M4Tl1W0edvF 6wYuuw7QiCWjHtPOEk4BDXl/IcV+vwyt+u2y4r8JZtTPW5Z+L83nzYNJmd8/WYMB XA7XZoRvtJvhzN2bzvYdftLl7B9E6Svk4OKSp+bqcD7MxZN1NowsEqOpL41tSXtC TDXXV8jTfJR0xFVQweug2af4qLCMNk6T7+m3x5aEAmGFnnvsaC0iN3XXn21304+v y4T7gZ0mSkHQqZ1CFUc+s1CfxAKWn9xC7et8rtIkUzySUZVuChdaWhvlQ5lQ05NL HOIsBYrT+VlaiZmznkdwYZ4EDLa3pB0w3Z0ld/LYH31x3EqC9+LqZ6RQCEAhWC3m oDU3zJyiI8khbybkQA+IGfU2+xXZEeQeQ4yUlvAZD8jWKzvmz4LwSS1m5IOPazP+ L0Eow+IEuQARAQABiQG2BBgBCgAgFiEEWXQiIxpzC/t0wUMKk1BzJpB1giAFAmjO VRwCGwwACgkQk1BzJpB1giAgOQwA0KTiW0yuVsny8iRUyRV7Q1EuClk4/CetF9wL pHcTbbz/wxu2SGO88NNUdNsp6NFWVL/qTPIn+vqfdcrtHXQGlLfdnOzi8dacf2yv ScRyBFf5sU3nRCTWyhPhInztjZ4O3Xov0EQy3YwRE44d5yAdhJA5KoHbZCVociDS Z1QpL9fXHNZKQBFFuTQ6GBKYi1AazYJLiqsOcRYJVBrqkD5F6cu4YLv6d0BoXEru 9/2V0ND4DuWCZ8KFJ0fTS7X1HiPaj1rCBMz8lI3dCfNUU5v3nrLjHB08YPTShJmJ Rj6fVvej8LM21VKOyCKGOyzT7abhnVoNNmpSqZhG0VkbZCth/wjs6Ifcw8hgotp5 6RcuwMm3xFu5ieuvli40betXWCnKhDj0UGbolEwabm7Qq1CHD6d6b8qtlZtd910B s/BCIKwOY7Oenpn0n+w+ilANdVjy614IrBtYNq1b1i2fOaTxI11XtpQ7KFgFQ4QW
7qRut0xZYIZV90BlCAWMlDdWlZiX =SoCq
-----END PGP PUBLIC KEY BLOCK-----
Mitigation Strategies
Recommended CE 5.5 Configuration Actions
- Block Nova Infrastructure: Add known Nova onion addresses to CE SWG blocklists.
- Enable CEASR Policies: Enforce application allowlisting and block execution from user-writeable directories.
- Configure SIEM Alerts: Create correlation rules for shadow copy deletion, mass encryption patterns, and qTox/Session traffic.
- Isolate Critical Assets: Apply micro-segmentation to separate AD, file servers, ESXi hosts, and backup infrastructure.
- Activate MDR Services: Enable Red Piranha's Incident Response Services for 24×7 SOC escalation and containment support.
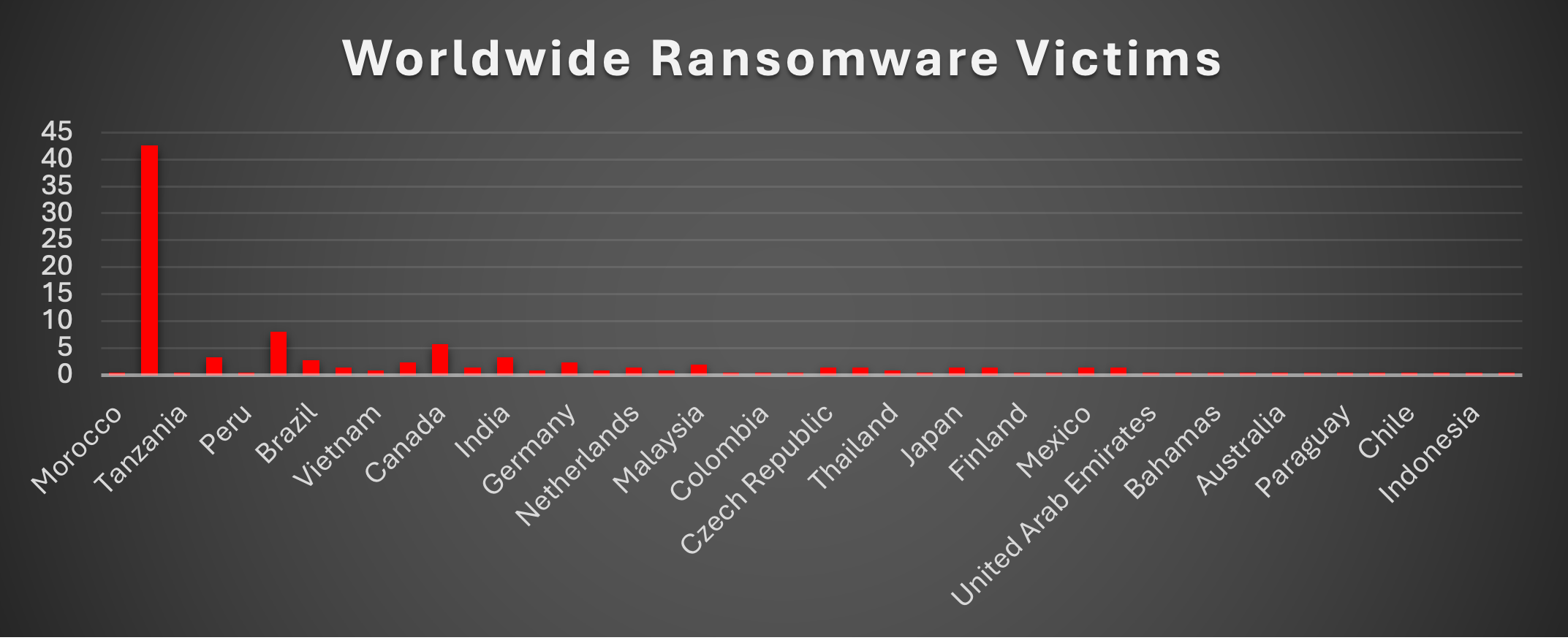
Worldwide Ransomware Victims by Country
Geographic distribution of ransomware victims shows the United States as the primary target (42.65%), followed by the United Kingdom (8.06%) and Canada (5.69%). European nations collectively represent a significant portion of victims, with growing activity in Asia-Pacific regions.
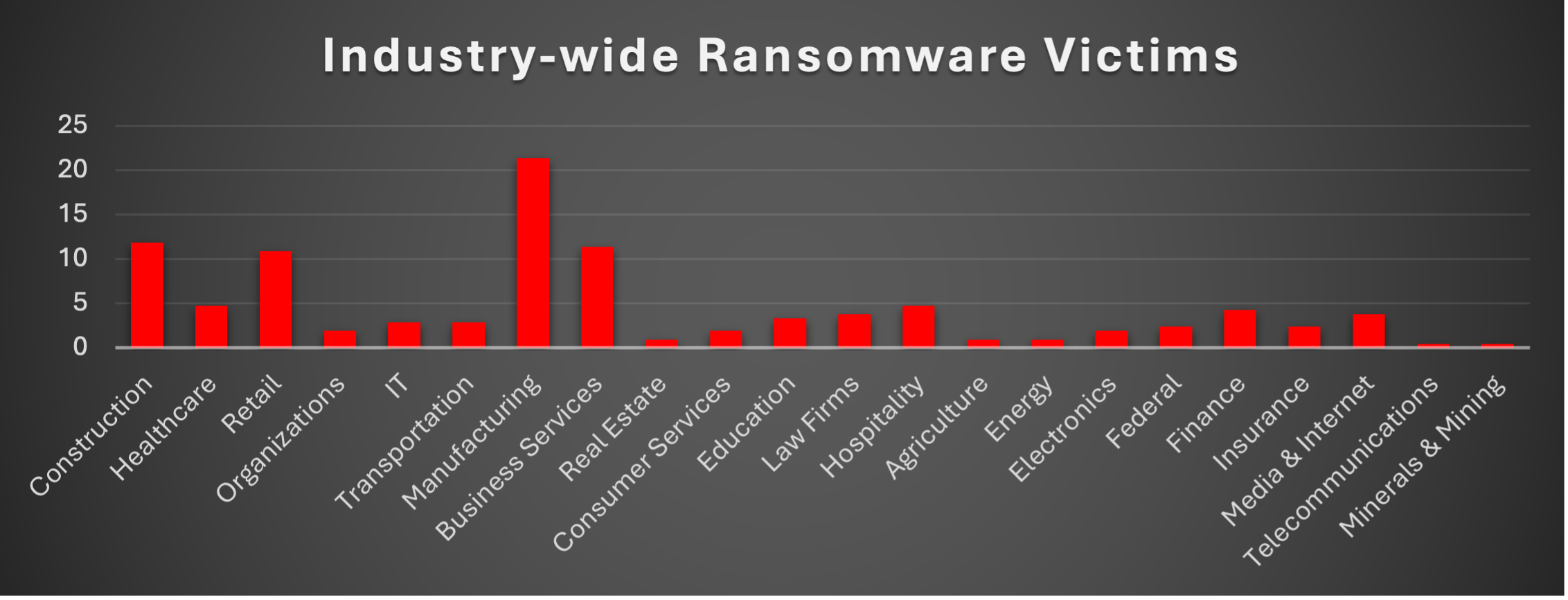
Industry-wide Ransomware Victims
Manufacturing leads as the most targeted sector (21.33%), followed by Construction (11.85%) and Business Services (11.37%). Healthcare (4.74%) and Finance (4.27%) remain high-value targets due to sensitive data holdings and operational criticality.